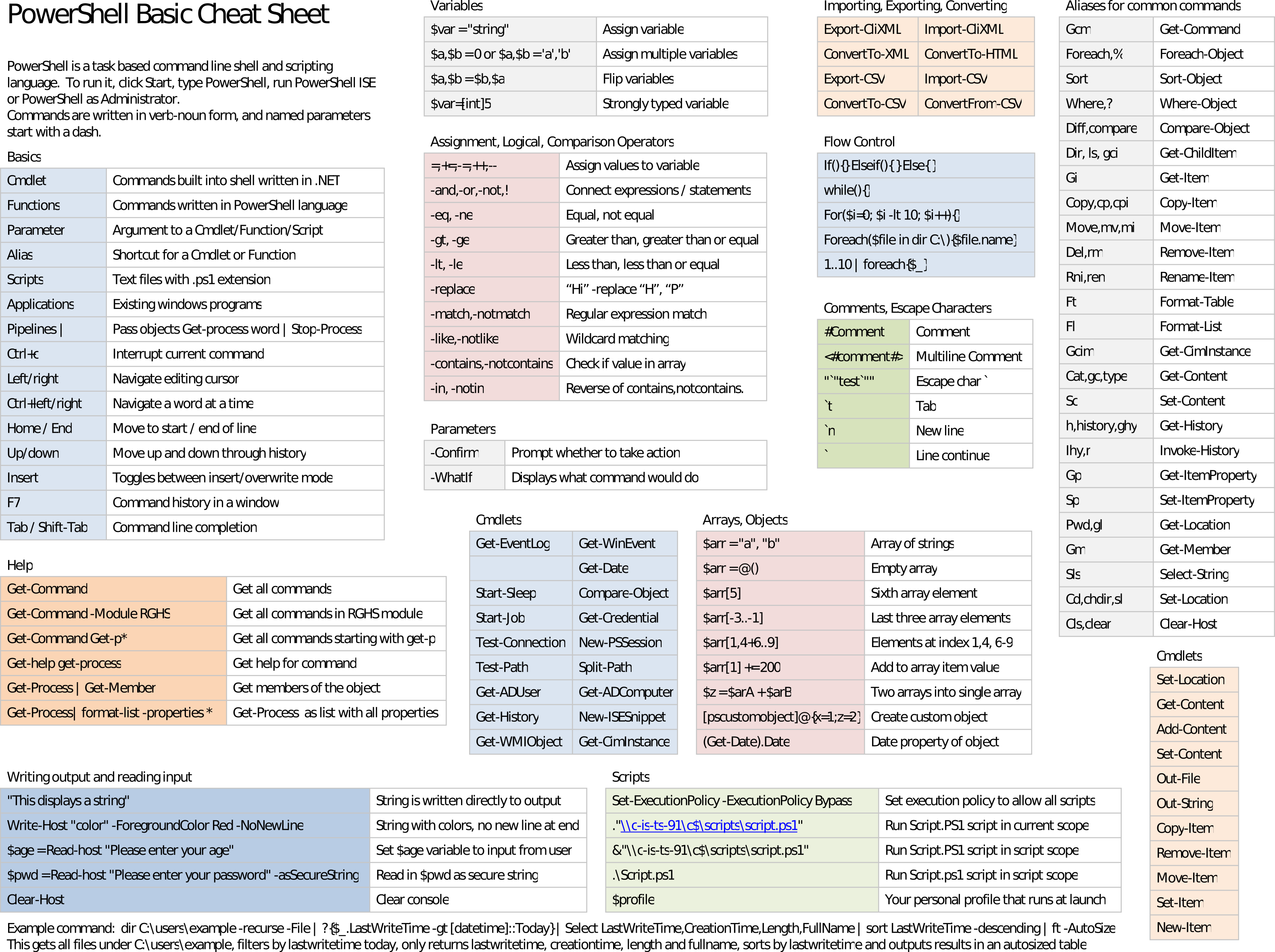
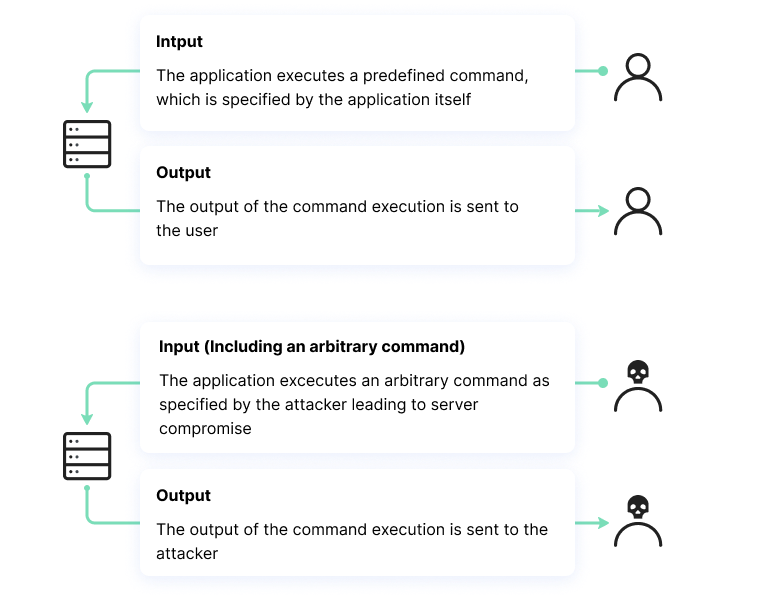
Command Injection Cheat Sheet - Learn what command injection is, how it works, and how to prevent it. A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems. See examples of vulnerable and exploitable code in c, java, and other. Visible results returned to the browser. Command injection provides control of server running with privileges of web apps. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep.
Learn what command injection is, how it works, and how to prevent it. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems. Command injection provides control of server running with privileges of web apps. Visible results returned to the browser. See examples of vulnerable and exploitable code in c, java, and other.
Learn what command injection is, how it works, and how to prevent it. A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems. See examples of vulnerable and exploitable code in c, java, and other. Visible results returned to the browser. Command injection provides control of server running with privileges of web apps. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep.
Os Command Injection Defense Owasp Cheat Sheet Series vrogue.co
Visible results returned to the browser. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. See examples of vulnerable and exploitable code in c, java, and other. Command injection provides control of server running with privileges of web apps. Learn what command injection is, how it works, and how to prevent it.
Command Injections Module Cheat Sheet PDF Computer Science Software
Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. Command injection provides control of server running with privileges of web apps. A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems. Learn what command injection is, how it works, and how to prevent it. See examples of vulnerable and.
Command Injection Cheatsheet PDF Character Encoding Computer
Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. Learn what command injection is, how it works, and how to prevent it. A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems. Visible results returned to the browser. See examples of vulnerable and exploitable code in c, java, and.
Os Command Injection Cheat Sheet sheet
Learn what command injection is, how it works, and how to prevent it. See examples of vulnerable and exploitable code in c, java, and other. Command injection provides control of server running with privileges of web apps. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. A collection of commands and payloads for.
Oracle SQL Injection Cheat Sheet SECURITY MASTER
Command injection provides control of server running with privileges of web apps. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. See examples of vulnerable and exploitable code in c, java, and other. Visible results returned to the browser. Learn what command injection is, how it works, and how to prevent it.
OS Command Injection Defense OWASP Cheat Sheet Series
Learn what command injection is, how it works, and how to prevent it. See examples of vulnerable and exploitable code in c, java, and other. Command injection provides control of server running with privileges of web apps. Visible results returned to the browser. A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems.
Os Command Injection Cheat Sheet sheet
A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems. Visible results returned to the browser. Command injection provides control of server running with privileges of web apps. See examples of vulnerable and exploitable code in c, java, and other. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep.
Os Command Injection Cheat Sheet sheet
See examples of vulnerable and exploitable code in c, java, and other. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. Command injection provides control of server running with privileges of web apps. Visible results returned to the browser. A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems.
Os Command Injection Cheat Sheet sheet
Learn what command injection is, how it works, and how to prevent it. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. Visible results returned to the browser. A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems. See examples of vulnerable and exploitable code in c, java, and.
Os Command Injection Cheat Sheet sheet
Command injection provides control of server running with privileges of web apps. Visible results returned to the browser. Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. See examples of vulnerable and exploitable code in c, java, and other. Learn what command injection is, how it works, and how to prevent it.
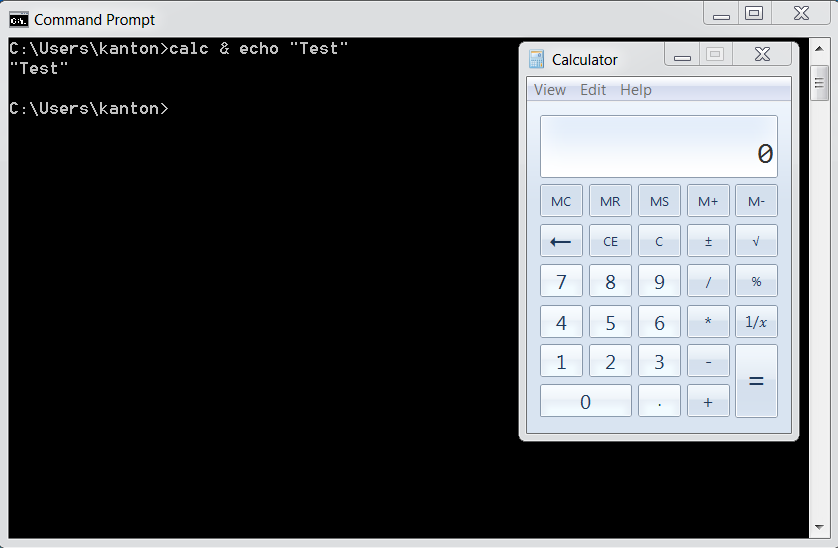
Visible Results Returned To The Browser.
Learn how to avoid command injection vulnerabilities in python code with this cheat sheet by semgrep. A collection of commands and payloads for exploiting command injection vulnerabilities in unix systems. Learn what command injection is, how it works, and how to prevent it. See examples of vulnerable and exploitable code in c, java, and other.